Authorization and Session Keys
Learn about session-based authorization in Okto SDK
Authorization in Okto SDK
Authorization in Okto SDK revolves around Session Keys - ephemeral cryptographic key pairs used to authenticate and authorize requests from your application to Okto services. Understanding how session keys are generated, managed, and used is crucial for building secure Okto-powered Web3 applications.
What is Session-Based Authentication?
Session management is a critical component of the Okto Ecosystem that provides a mechanism for applications to interact with Okto services without requiring the user's private key for every transaction. By employing ephemeral session keys, Okto minimizes the exposure of long-term credentials while enabling a seamless Web2-like experience.
Note
Session keys are valid for 10 days. If a user logs out or the session expires, new session keys must be generated.
How Session Key Authentication Works
Login and Session Initialization
When a user logs in, the following sequence takes place:
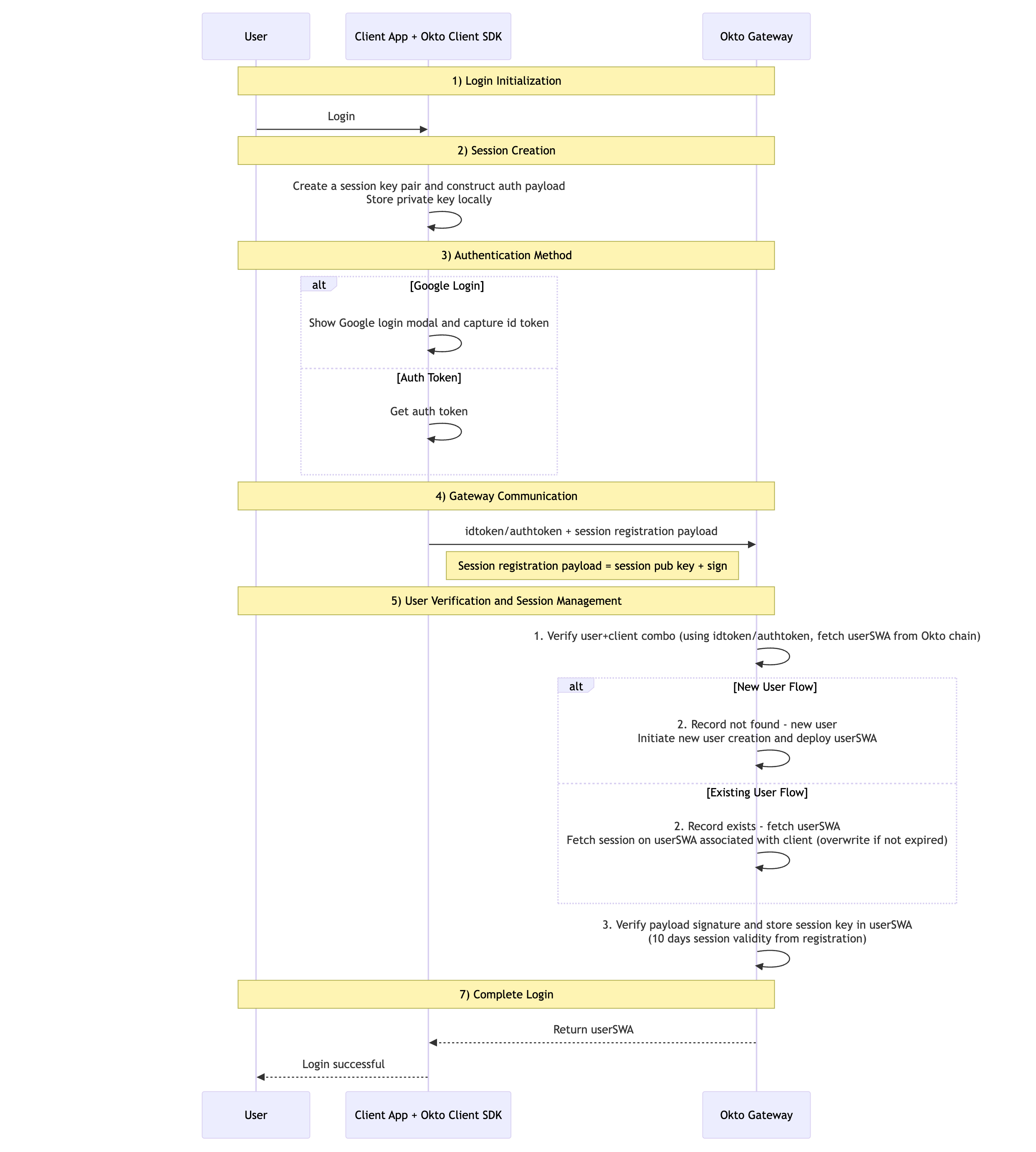
In this process:
-
Client-Side Session Key Generation: When a user initiates a login through a client application, the SDK automatically generates a unique session key pair behind the scenes.
-
Authentication Request: The SDK constructs an authentication payload containing the user's credentials and necessary session information. The client application then sends the authentication payload along with the session public key to Okto.
-
User Verification and Setup: Okto Chain verifies the user's credentials and either creates a new Smart Wallet Account (SWA) for new users or fetches the existing SWA for returning users.
-
Session Establishment: Upon successful authentication, the session is established with a 10-day validity period and linked to the user's Smart Wallet Account (SWA).
Intent Operation
Once a user is authenticated, the client application can perform operations on their behalf using the session keys without additional login steps:
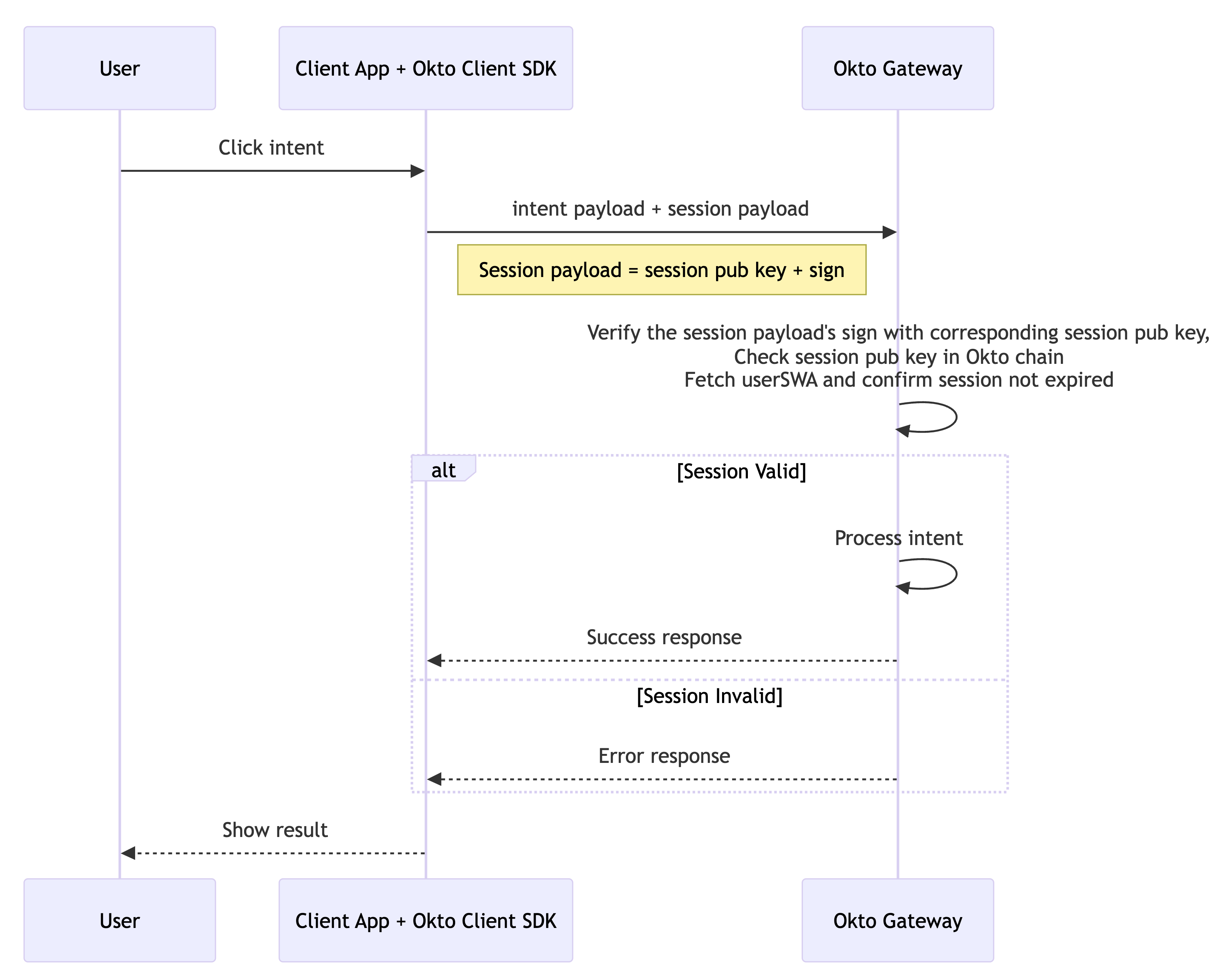
In this process:
-
User Initiates Action: The user performs an action in a client application that requires blockchain interaction.
-
Intent Generation: The SDK generates the appropriate intent payload with the necessary operation details.
-
Session Authentication: The intent is sent to Okto along with the session key signature for authentication.
-
Verification and Execution: Okto verifies the session validity and processes the intent if the session is valid.
Delegated Intent Execution
Okto also supports delegated intents, where applications can execute operations on behalf of users without direct user interaction:
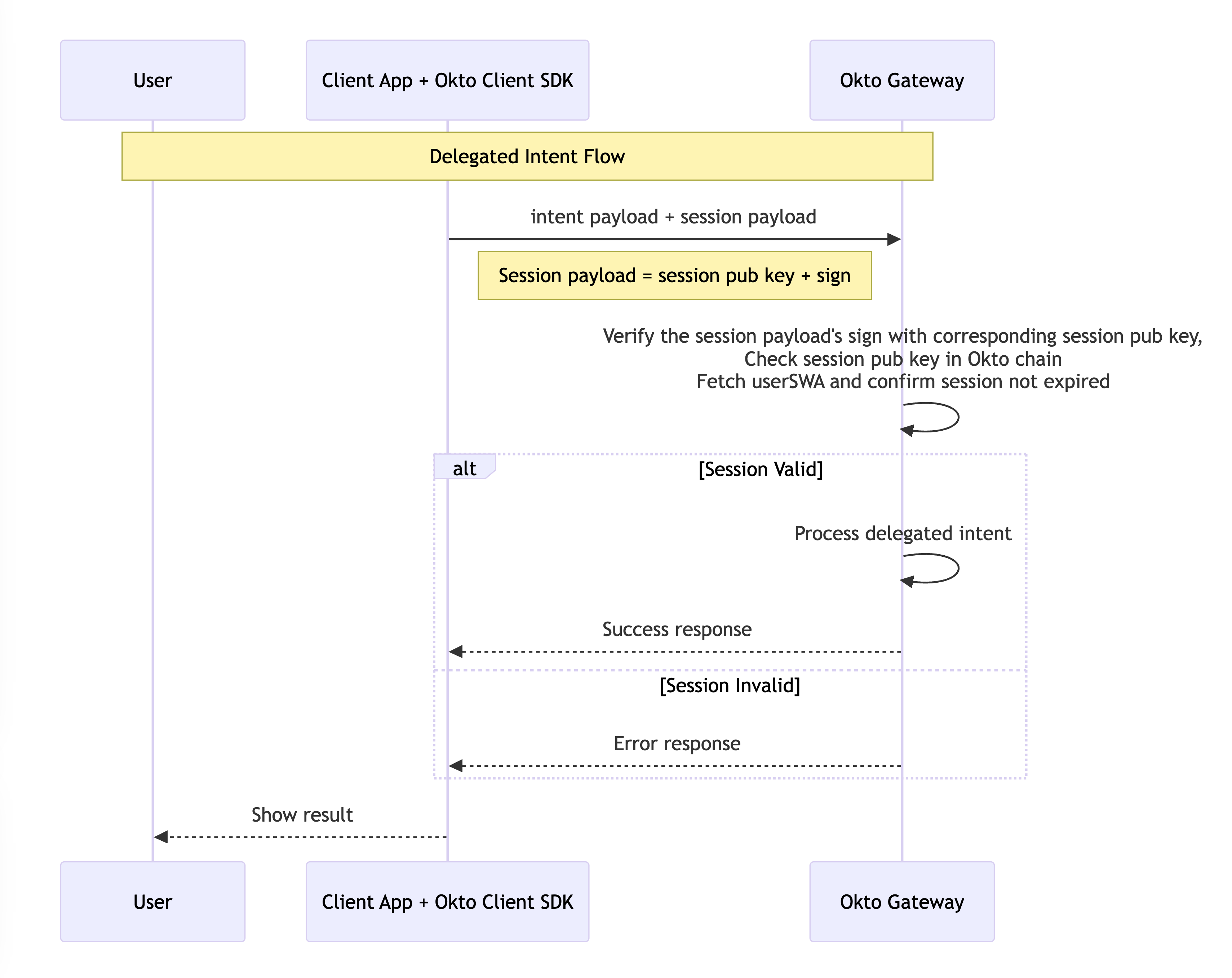
This process allows for:
-
Automatic Execution: Intents can be executed automatically by the client applicationwhen certain conditions are met.
-
Policy-Based Control: The execution can be governed by policies that set limits on transaction values or frequencies.
-
Improved User Experience: Users don't need to approve each transaction, creating a Web2-like experience in Web3 applications.
Next Steps
Learn more about authentication methods and session management:
- Google OAuth Authentication - Implement secure authentication using Google OAuth
- Session Management - Handle user sessions and state management